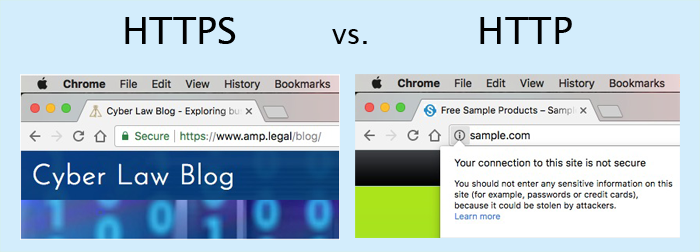
Most states have data breach laws that require companies to secure the personal data of their customers, yet WIRED reported that only 50% of websites use the Internet’s secure HTTPS protocol. With the release of Chrome v62, Google is requiring websites to use HTTPS (Hyper Text Transfer Protocol Secure) that encrypts data with SSL (Secure Sockets Layer). If a website is not secure, Google will lower its rankings in the search engine.
HTTP Transmits Clear Text
When a website allows a user to input text into a web form, it transmits the text from the user’s web browser to the web server. A website that uses HTTP (Hyper Text Transfer Protocol) transmits text in a “clear text” format, which leaves the data vulnerable for hacker attacks.
Using a network sniffer utility, a hacker can intercept the clear text that is traveling through the web. For example, Wireshark, a network protocol analyzer, captures packets of data by sniffing a network for traffic. Using Wireshark, a hacker can sniff a network, capture the traffic, and display the data in a readable format.
While HTTP operates on port 80, HTTPS creates a secure tunnel using SSL port 443. Importantly, HTTPS is stateful, which means it establishes a connection between the web browser and the web server until the session is complete.
HTTPS Compliance
To implement SSL, a website owner must obtain an SSL certificate from a trusted Certificate Authority. Next, the web administrator installs the certificate on the web server and configures the website to use the HTTPS protocol.
Google has a strategy to enforce the SSL requirement. If a website lacks an SSL certificate, the Chrome browser will tag it as “not secure.” Additionally, Google plans to favor websites in its search engine rankings that use HTTPS.
SSL Vulnerabilities and Benefits
A motivated hacker may still be able to find a way to defeat HTTPS. For example, once a HTTPS session creates an SSL tunnel, the contents are encrypted and sent through the tunnel bypassing any content filtering appliance. This means that malware could travel through the tunnel without being noticed. An unaware web client would download the malware, and it could replicate itself across the network. As a defense, a network administrator can setup a proxy server using SSL Inspection to prevent this type of attack.
Although HTTPS has vulnerabilities, transmitting encrypted data is preferable to sending it through the web in clear text. In addition to the security benefits, using HTTPS offers better search engine rankings and verifies the authenticity of the website.